 |
经鉴定,楼主是折腾骨头版PE的骨灰级专家 |
|
winxshell默认的自带的文件管理器!  |
本帖最后由 sairen139 于 2023-6-29 23:32 编辑 sairen139 发表于 2022-10-27 22:05 经测试winxshell的自带资源管理器右上角搜索需要下面四个依赖文件 \Windows\System32\MSWB70804.dll \Windows\System32\NL7Data0804.dll \Windows\System32\SearchFolder.dll \Windows\System32\Windows.Storage.Search.dll 这四个文件体积5mb多有点大,不如用几百k的JustManager搜索替代或者1mb多的explorer++的搜索替代。或者用搜索速度最快的Everything取代pe搜索功能! |
sairen139 发表于 2022-10-27 22:05 文件夹浏览模式平铺还是详细信息列表的喜好选择。平铺会名字长折成两行可直接预览,缺点占面积大。详细列表同面积内信息量大但每个只一行。pe里选哪个好可以选喜欢的设置好然后导出以下的注册表! HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Streams\Defaults 设置好后导出这个注册表 |
本帖最后由 sairen139 于 2022-11-12 08:40 编辑 sairen139 发表于 2022-10-27 22:05 玩江南疯牛病专修版选原生bat,结果打不开winxshell自带资源管理器了。江南发现是精简software的锅,提供了修补的离线注册表如下: 离线修复winxshell自带类资源管理器不能打开.reg Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Classes\CLSID\{DC1C5A9C-E88A-4dde-A5A1-60F82A20AEF7}] @="File Open Dialog" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Classes\CLSID\{DC1C5A9C-E88A-4dde-A5A1-60F82A20AEF7}\InProcServer32] @=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,00,25,\ 00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,63,00,6f,00,\ 6d,00,64,00,6c,00,67,00,33,00,32,00,2e,00,64,00,6c,00,6c,00,00,00 "ThreadingModel"="Apartment" 离线补回winxshell自带类资源管理器里的组织按钮和功能列表.reg Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore] [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell] [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.aboutWindows] "CanonicalName"="{20E8B2FE-7568-46AE-A0DB-76B7F469B92D}" "Description"="@explorerframe.dll,-14403" "Icon"=hex(2):69,00,6d,00,61,00,67,00,65,00,72,00,65,00,73,00,2e,00,64,00,6c,\ 00,6c,00,2c,00,2d,00,38,00,31,00,00,00 "MUIVerb"="@explorerframe.dll,-14402" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.aboutWindows\command] "DelegateExecute"="{20E8B2FE-7568-46AE-A0DB-76B7F469B92D}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.AddColumns] "CommandStateSync"="" "Description"="@shell32.dll,-37465" "ExplorerCommandHandler"="{385906fb-1482-4f64-8a23-5d74e1ce1815}" "Icon"="imageres.dll,-5313" "MUIVerb"="@shell32.dll,-37464" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.AddDevice] "CanonicalName"="{6eec5029-6475-411d-8037-532aafb457a7}" "CommandStateHandler"="{E410F8AE-00A1-4A1B-8247-924705718354}" "CommandStateSync"="" "Description"=hex(2):40,00,25,00,73,00,79,00,73,00,74,00,65,00,6d,00,72,00,6f,\ 00,6f,00,74,00,25,00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,\ 5c,00,4e,00,65,00,74,00,77,00,6f,00,72,00,6b,00,45,00,78,00,70,00,6c,00,6f,\ 00,72,00,65,00,72,00,2e,00,64,00,6c,00,6c,00,2c,00,2d,00,31,00,30,00,35,00,\ 31,00,00,00 "FolderHandler"="{D20BEEC4-5CA8-4905-AE3B-BF251EA09B53}" "Icon"="imageres.dll,-5363" "MUIVerb"=hex(2):40,00,25,00,73,00,79,00,73,00,74,00,65,00,6d,00,72,00,6f,00,\ 6f,00,74,00,25,00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,\ 00,4e,00,65,00,74,00,77,00,6f,00,72,00,6b,00,45,00,78,00,70,00,6c,00,6f,00,\ 72,00,65,00,72,00,2e,00,64,00,6c,00,6c,00,2c,00,2d,00,31,00,30,00,35,00,30,\ 00,00,00 "VerbHandler"="{0702A4F1-F97B-410d-9D53-0911741AC442}" "VerbName"="AddDevice" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.AddDevice\command] "DelegateExecute"="{E410F8AE-00A1-4A1B-8247-924705718354}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.AddMediaServer] "CommandStateSync"="" "ExplorerCommandHandler"="{d7bfd8f3-678c-4827-b84b-0e5fc6d15be3}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.AddNetworkLocation] "CanonicalName"="{E282A195-959F-4630-9A9F-AA97BFCEDE22}" "Description"="@shell32.dll,-31303" "Icon"="shell32.dll,-176" "MUIVerb"="@shell32.dll,-31302" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.AddNetworkLocation\command] @=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,00,25,\ 00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,72,00,75,00,\ 6e,00,64,00,6c,00,6c,00,33,00,32,00,20,00,25,00,53,00,79,00,73,00,74,00,65,\ 00,6d,00,52,00,6f,00,6f,00,74,00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,\ 6d,00,33,00,32,00,5c,00,73,00,68,00,77,00,65,00,62,00,73,00,76,00,63,00,2e,\ 00,64,00,6c,00,6c,00,2c,00,41,00,64,00,64,00,4e,00,65,00,74,00,50,00,6c,00,\ 61,00,63,00,65,00,52,00,75,00,6e,00,44,00,6c,00,6c,00,00,00 [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.AddPrinter] "CanonicalName"="{3349E8A8-B846-4E22-BE2B-62833A1D429D}" "Description"=hex(2):40,00,25,00,73,00,79,00,73,00,74,00,65,00,6d,00,72,00,6f,\ 00,6f,00,74,00,25,00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,\ 5c,00,44,00,65,00,76,00,69,00,63,00,65,00,43,00,65,00,6e,00,74,00,65,00,72,\ 00,2e,00,64,00,6c,00,6c,00,2c,00,2d,00,35,00,32,00,33,00,00,00 "Icon"=hex(2):73,00,68,00,65,00,6c,00,6c,00,33,00,32,00,2e,00,64,00,6c,00,6c,\ 00,2c,00,2d,00,31,00,37,00,00,00 "MUIVerb"=hex(2):40,00,25,00,73,00,79,00,73,00,74,00,65,00,6d,00,72,00,6f,00,\ 6f,00,74,00,25,00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,\ 00,44,00,65,00,76,00,69,00,63,00,65,00,43,00,65,00,6e,00,74,00,65,00,72,00,\ 2e,00,64,00,6c,00,6c,00,2c,00,2d,00,35,00,30,00,33,00,00,00 [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.AddPrinter\command] @=hex(2):25,00,73,00,79,00,73,00,74,00,65,00,6d,00,72,00,6f,00,6f,00,74,00,25,\ 00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,72,00,75,00,\ 6e,00,64,00,6c,00,6c,00,33,00,32,00,2e,00,65,00,78,00,65,00,20,00,70,00,72,\ 00,69,00,6e,00,74,00,75,00,69,00,2e,00,64,00,6c,00,6c,00,2c,00,50,00,72,00,\ 69,00,6e,00,74,00,55,00,49,00,45,00,6e,00,74,00,72,00,79,00,20,00,2f,00,69,\ 00,6c,00,00,00 [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.AddRemovePrograms] "CanonicalName"="{4E2C075C-1CC1-4E0C-BF69-D0317B8F9539}" "CommandStateHandler"="{E410F8AE-00A1-4A1B-8247-924705718354}" "CommandStateSync"="" "Description"="@shell32.dll,-31328" "FolderHandler"="{0AC0837C-BBF8-452A-850D-79D08E667CA7}" "Icon"="shell32.dll,-271" "MUIVerb"="@shell32.dll,-31327" "VerbHandler"="{a2e6d9cc-f866-40b6-a4b2-ee9e1004bdfc}" "VerbName"="AddRemovePrograms" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.AddRemovePrograms\command] "DelegateExecute"="{E410F8AE-00A1-4A1B-8247-924705718354}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.AddToFavorites] "CanonicalName"="{0A21CB3A-24E0-49E6-8E6C-49C59E6CD085}" "CommandStateSync"="" "Description"="@shell32.dll,-37409" "ExplorerCommandHandler"="{323CA680-C24D-4099-B94D-446DD2D7249E}" "Icon"="shell32.dll,-322" "ImpliedSelectionModel"=dword:00000021 "MUIVerb"="@shell32.dll,-37408" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.Autoplay] "CanonicalName"="{702E0142-7A90-4E8B-A6DC-EC1184C3EF18}" "CommandStateHandler"="{E410F8AE-00A1-4A1B-8247-924705718354}" "CommandStateSync"="" "Description"="@shell32.dll,-31388" "FolderHandler"="{0AC0837C-BBF8-452A-850D-79D08E667CA7}" "Icon"="imageres.dll,-5362" "ImpliedSelectionModel"=dword:00000001 "MUIVerb"="@shell32.dll,-31384" "ResolveLinksQueryBehavior"=dword:00000000 "VerbHandler"="{FE7D1066-E76F-44be-B73D-D1BF667F6D00}" "VerbName"="autoplay" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.Autoplay\command] "DelegateExecute"="{E410F8AE-00A1-4A1B-8247-924705718354}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.Backup] "CommandStateSync"="" "ExplorerCommandHandler"="{d1934e71-740b-47cf-b051-6551e5b80fd5}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.BitLocker] "CanonicalName"="be76fd37-dd51-4336-888e-dcd4d3a46e08}" "Description"="@%SystemRoot%\\System32\\fvewiz.dll,-976" "ExplorerCommandHandler"="{AFA470FE-371D-4F98-9592-39E3C7227E5C}" "Icon"="%SystemRoot%\\System32\\fvewiz.dll,-3" "ImpliedSelectionModel"=dword:00000001 "MUIVerb"=hex(2):40,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,\ 6f,00,74,00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,\ 00,66,00,76,00,65,00,77,00,69,00,7a,00,2e,00,64,00,6c,00,6c,00,2c,00,2d,00,\ 39,00,37,00,32,00,00,00 "VerbList"=hex(7):57,00,69,00,6e,00,64,00,6f,00,77,00,73,00,2e,00,42,00,69,00,\ 74,00,4c,00,6f,00,63,00,6b,00,65,00,72,00,2e,00,45,00,6e,00,63,00,72,00,79,\ 00,70,00,74,00,00,00,57,00,69,00,6e,00,64,00,6f,00,77,00,73,00,2e,00,42,00,\ 69,00,74,00,4c,00,6f,00,63,00,6b,00,65,00,72,00,2e,00,4d,00,61,00,6e,00,61,\ 00,67,00,65,00,00,00,57,00,69,00,6e,00,64,00,6f,00,77,00,73,00,2e,00,42,00,\ 69,00,74,00,4c,00,6f,00,63,00,6b,00,65,00,72,00,2e,00,52,00,65,00,73,00,65,\ 00,74,00,50,00,61,00,73,00,73,00,77,00,6f,00,72,00,64,00,50,00,69,00,6e,00,\ 00,00,00,00 [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.BitLocker.Encrypt] "CanonicalName"="{06d95fe9-7eec-4ed7-bb84-f6784cd1175c}" "ExplorerCommandHandler"="{AFA470FE-371D-4F98-9592-39E3C7227E5C}" "Icon"="imageres.dll,-5381" "ImpliedSelectionModel"=dword:00000001 "MUIVerb"=hex(2):40,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,\ 6f,00,74,00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,\ 00,66,00,76,00,65,00,77,00,69,00,7a,00,2e,00,64,00,6c,00,6c,00,2c,00,2d,00,\ 39,00,37,00,33,00,00,00 "VerbList"=hex(7):57,00,69,00,6e,00,64,00,6f,00,77,00,73,00,2e,00,65,00,6e,00,\ 63,00,72,00,79,00,70,00,74,00,2d,00,62,00,64,00,65,00,2d,00,65,00,6c,00,65,\ 00,76,00,00,00,57,00,69,00,6e,00,64,00,6f,00,77,00,73,00,2e,00,65,00,6e,00,\ 63,00,72,00,79,00,70,00,74,00,2d,00,62,00,64,00,65,00,00,00,00,00 [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.BitLocker.Manage] "CanonicalName"="{c6fddf41-94be-4b2f-8f1c-fd6a07feb7df}" "ExplorerCommandHandler"="{AFA470FE-371D-4F98-9592-39E3C7227E5C}" "Icon"="imageres.dll,-5364" "ImpliedSelectionModel"=dword:00000001 "MUIVerb"=hex(2):40,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,\ 6f,00,74,00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,\ 00,66,00,76,00,65,00,77,00,69,00,7a,00,2e,00,64,00,6c,00,6c,00,2c,00,2d,00,\ 39,00,37,00,34,00,00,00 "VerbList"=hex(7):57,00,69,00,6e,00,64,00,6f,00,77,00,73,00,2e,00,6d,00,61,00,\ 6e,00,61,00,67,00,65,00,2d,00,62,00,64,00,65,00,2d,00,65,00,6c,00,65,00,76,\ 00,00,00,57,00,69,00,6e,00,64,00,6f,00,77,00,73,00,2e,00,6d,00,61,00,6e,00,\ 61,00,67,00,65,00,2d,00,62,00,64,00,65,00,00,00,00,00 [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.BitLocker.ResetPasswordPin] "CanonicalName"="{dc7f00b2-a808-40ff-8440-ac8d2f4341f1}" "ExplorerCommandHandler"="{AFA470FE-371D-4F98-9592-39E3C7227E5C}" "Icon"="imageres.dll,-5360" "ImpliedSelectionModel"=dword:00000001 "MUIVerb"=hex(2):40,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,\ 6f,00,74,00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,\ 00,66,00,76,00,65,00,77,00,69,00,7a,00,2e,00,64,00,6c,00,6c,00,2c,00,2d,00,\ 39,00,37,00,35,00,00,00 "VerbList"=hex(7):57,00,69,00,6e,00,64,00,6f,00,77,00,73,00,2e,00,63,00,68,00,\ 61,00,6e,00,67,00,65,00,2d,00,70,00,61,00,73,00,73,00,70,00,68,00,72,00,61,\ 00,73,00,65,00,00,00,57,00,69,00,6e,00,64,00,6f,00,77,00,73,00,2e,00,63,00,\ 68,00,61,00,6e,00,67,00,65,00,2d,00,70,00,69,00,6e,00,00,00,00,00 [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.burn] "CanonicalName"="{c501e86c-b7e3-4667-95c5-73872080c0a8}" "CommandStateHandler"="{3756e7f5-e514-4776-a32b-eb24bc1efe7a}" "CommandStateSync"="" "Description"="@shell32.dll,-31356" "Icon"="shell32.dll,-260" "MUIVerb"="@shell32.dll,-31355" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.burn\command] "DelegateExecute"="{b91a4db4-3630-11dc-9eaa-00161718cf63}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.Burn.Action] "ActionId"="Explorer.BurnSelection" "CanonicalName"="{BDE1B3A4-5A4E-44DB-9170-7935DD7D6163}" "CommandStateSync"="" "CommandStore"="Windows.burn" "ExplorerCommandHandler"="{9C07355E-C50A-45D2-B4A3-0A8235F8047F}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.change-passphrase] "CanonicalName"="{303fd22e-2d83-4013-8d2c-bb489ee09563}" "InvokeCommandOnSelection"=dword:00000001 "MUIVerb"=hex(2):40,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,\ 6f,00,74,00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,\ 00,66,00,76,00,65,00,77,00,69,00,7a,00,2e,00,64,00,6c,00,6c,00,2c,00,2d,00,\ 39,00,37,00,31,00,00,00 "StaticVerbOnly"="" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.change-pin] "CanonicalName"="{65b55c76-cd33-40b0-9679-cae3876dba13}" "InvokeCommandOnSelection"=dword:00000001 "MUIVerb"=hex(2):40,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,\ 6f,00,74,00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,\ 00,66,00,76,00,65,00,77,00,69,00,7a,00,2e,00,64,00,6c,00,6c,00,2c,00,2d,00,\ 39,00,37,00,30,00,00,00 "StaticVerbOnly"="" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.ChangeIndexedLocations] "CanonicalName"="{34ac91ce-75cc-4c40-a4bc-e352528d3cbd}" "ControlPanelName"="Microsoft.IndexingOptions" "Description"="@shell32.dll,-37536" "MUIVerb"="@shell32.dll,-37535" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.ChangeIndexedLocations\Command] "DelegateExecute"="{06622D85-6856-4460-8DE1-A81921B41C4B}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.ChooseColumns] "Description"="@shell32.dll,-37577" "ExplorerCommandHandler"="{1c391f2b-801a-416c-9838-6be810293dfc}" "MUIVerb"="@shell32.dll,-37576" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.CleanUp] "CommandStateSync"="" "ExplorerCommandHandler"="{9cca66bb-9c78-4e59-a76f-a5e9990b8aa0}" "Icon"="%SystemRoot%\\System32\\cleanmgr.exe,-104" "ImpliedSelectionModel"=dword:00000001 [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.ClearAddressBarHistory] "CanonicalName"="{935249A5-B5E8-43F6-A991-61435E5954B3}" "Description"="@explorerframe.dll,-14401" "Icon"="imageres.dll,-5319" "MUIVerb"="@explorerframe.dll,-14400" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.ClearAddressBarHistory\command] "DelegateExecute"="{935249A5-B5E8-43F6-A991-61435E5954B3}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.ClearFrequentHistory] "Description"="@shell32,-37443" "MUIVerb"="@shell32,-37442" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.clearRecentDocs] "CanonicalName"="{2F096B28-C65D-4C05-A37E-7E88735E32FA}" "Description"="@shell32,-10562" "Icon"="imageres.dll,-5318" "MUIVerb"="@shell32,-37410" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.clearRecentDocs\command] "DelegateExecute"="{2F096B28-C65D-4C05-A37E-7E88735E32FA}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.closewindow] "CanonicalName"="{edf99fce-5d83-441a-a6c6-d363532ede4f}" "CommandStateHandler"="{3756e7f5-e514-4776-a32b-eb24bc1efe7a}" "CommandStateSync"="" "Description"="@shell32.dll,-31451" "Icon"="imageres.dll,-5320" "MUIVerb"="@shell32.dll,-31450" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.closewindow\command] "DelegateExecute"="{8570b44e-d109-42d3-be32-0f8d446669c5}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.cmd] "CanonicalName"="{858B5A19-A5CE-40CE-9FA7-44C4254BA4A0}" "Description"="@shell32.dll,-37416" "Icon"="imageres.dll,-5323" "ImpliedSelectionModel"=dword:00000001 "InvokeCommandOnSelection"=dword:00000001 "MUIVerb"="@shell32.dll,-37415" "ResolveLinksQueryBehavior"=dword:00000000 "StaticVerbOnly"="" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.cmdPromptAsAdministrator] "CanonicalName"="{8133CB32-451F-4A9F-9B90-F6F80FCE6348}" "CommandStateSync"="" "Description"="@shell32.dll,-37445" "ExplorerCommandHandler"="{858DACA2-78B4-412F-9A4E-315BBB4E1F21}" "Icon"="imageres.dll,-5324" "ImpliedSelectionModel"=dword:00000001 "MUIVerb"="@shell32.dll,-37444" "ResolveLinksInvokeBehavior"=dword:00000003 "ResolveLinksQueryBehavior"=dword:00000000 [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.CompressedFile.extract] "CanonicalName"="{af01f534-9beb-4d8c-b729-ddf4e2579f31}" "CommandStateSync"="" "Description"="@shell32.dll,-37515" "ExplorerCommandHandler"="{AFA470FE-371D-4F98-9592-39E3C7227E5C}" "Icon"="imageres.dll,-5327" "MUIVerb"="@shell32.dll,-37514" "VerbList"=hex(7):57,00,69,00,6e,00,64,00,6f,00,77,00,73,00,2e,00,43,00,6f,00,\ 6d,00,70,00,72,00,65,00,73,00,73,00,65,00,64,00,46,00,6f,00,6c,00,64,00,65,\ 00,72,00,2e,00,65,00,78,00,74,00,72,00,61,00,63,00,74,00,00,00,57,00,69,00,\ 6e,00,64,00,6f,00,77,00,73,00,2e,00,43,00,6f,00,6d,00,70,00,72,00,65,00,73,\ 00,73,00,65,00,64,00,49,00,74,00,65,00,6d,00,2e,00,65,00,78,00,74,00,72,00,\ 61,00,63,00,74,00,00,00,00,00 [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.CompressedFile.ExtractTo] "CommandStateSync"="" "Description"="@shell32.dll,-37517" "ExplorerCommandHandler"="{2737EE87-ABA3-4F28-89A6-C370484D85F9}" "Icon"="imageres.dll,-5304" "MUIVerb"="@shell32.dll,-37516" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.CompressedFolder.extract] "ImpliedSelectionModel"=dword:00000044 "InvokeCommandOnSelection"=dword:00000001 "StaticVerbOnly"="" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.CompressedItem.extract] "InvokeCommandOnSelection"=dword:00000001 "IsInContextMenu"="" "ResolveLinksQueryBehavior"=dword:00000000 [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.Computer.Manage] "CanonicalName"="{d577c470-5769-4467-9e71-a14b4a659aa7}" "Description"="@shell32.dll,-37603" "FolderHandler"="{0AC0837C-BBF8-452A-850D-79D08E667CA7}" "Icon"="imageres.dll,-5374" "InvokeCommandOnSelection"=dword:00000001 "MUIVerb"="@shell32.dll,-37602" "StaticVerbOnly"="" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.connectNetworkDrive] "CanonicalName"="{87B6B49A-4106-421E-9293-5FFC4B1D679C}" "CommandStateSync"="" "Description"="@shell32.dll,-37441" "ExplorerCommandHandler"="{b7373566-8ff2-45d8-af1f-da39f289bcf9}" "Icon"="imageres.dll,-5326" "InvokeCommandOnSelection"=dword:00000001 "MUIVerb"="@shell32.dll,-37440" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.copy] "AttributeMask"=dword:00000001 "AttributeValue"=dword:00000001 "CanonicalName"="{F0FF2AE6-3A15-48C3-98F2-FEBE2BA780D8}" "Description"="@shell32.dll,-31247" "Icon"="shell32.dll,-243" "ImpliedSelectionModel"=dword:00000000 "InvokeCommandOnSelection"=dword:00000001 "MUIVerb"="@shell32.dll,-31246" "ShowAsDisabledIfHidden"="" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.copyaspath] "CanonicalName"="{707C7BC6-685A-4A4D-A275-3966A5A3EFAA}" "CommandStateHandler"="{3B1599F9-E00A-4BBF-AD3E-B3F99FA87779}" "CommandStateSync"="" "Description"="@shell32.dll,-30336" "Icon"="imageres.dll,-5302" "InvokeCommandOnSelection"=dword:00000001 "MUIVerb"="@shell32.dll,-30329" "VerbHandler"="{f3d06e7c-1e45-4a26-847e-f9fcdee59be0}" "VerbName"="copyaspath" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.CopyToBrowser] "CommandStateSync"="" "ExplorerCommandHandler"="{AF65E2EA-3739-4e57-9C5F-7F43C949CE5E}" "Icon"="imageres.dll,-5382" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.CopyToMenu] "CommandStateSync"="" "ExplorerCommandHandler"="{3852C2E2-4A16-4b11-8E71-F8904C37EC3D}" "Icon"="imageres.dll,-5304" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.CscSync] "ExplorerCommandHandler"="{09017262-fdb4-4ff2-9013-26332c926ee7}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.CscWorkOfflineOnline] "ExplorerCommandHandler"="{196f128d-dce9-4090-b061-3d29c6ca32c2}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.cut] "AttributeMask"=dword:00000002 "AttributeValue"=dword:00000002 "CanonicalName"="{fdadbe2d-b1d6-476b-85bd-5929b017cc00}" "Description"="@shell32.dll,-31245" "Icon"="shell32.dll,-16762" "ImpliedSelectionModel"=dword:00000000 "InvokeCommandOnSelection"=dword:00000001 "MUIVerb"="@shell32.dll,-31244" "ShowAsDisabledIfHidden"="" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.Defragment] "CommandStateSync"="" "ExplorerCommandHandler"="{5D75245F-29AE-450D-8924-A7611DE279AF}" "Icon"="shell32.dll,-167" "ImpliedSelectionModel"=dword:00000001 [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.delete] "AttributeMask"=dword:00000020 "AttributeValue"=dword:00000020 "CanonicalName"="{9ED8204C-C3DE-4D66-9851-42943F9FCC77}" "Description"="@shell32.dll,-31253" "Icon"="shell32.dll,-240" "ImpliedSelectionModel"=dword:00000000 "InvokeCommandOnSelection"=dword:00000001 "MUIVerb"="@shell32.dll,-31252" "ShowAsDisabledIfHidden"="" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.Dialog.DisconnectNetworkDrive] "CanonicalName"="{D176D321-AACF-4329-BFFA-13F1DD14FE2A}" "FolderHandler"="{0AC0837C-BBF8-452A-850D-79D08E667CA7}" "InvokeCommandOnSelection"=dword:00000001 "StaticVerbOnly"="" "VerbName"="disconnectNetworkDrive" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.DiscImage.burn] "CanonicalName"="{5A6D5871-AD2A-4E06-8637-065A8062CF01}" "Description"="@shell32.dll,-38305" "Icon"="shell32.dll,-260" "InvokeCommandOnSelection"=dword:00000001 "MUIVerb"="@shell32.dll,-38304" "ResolveLinksQueryBehavior"=dword:00000000 "StaticVerbOnly"="" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.DisconnectNetworkDrive] "CanonicalName"="{F8975BDE-E9F1-405C-BFD1-8D2E7F0D5D0F}" "CommandStateSync"="" "Description"="@shell32.dll,-31305" "ExplorerCommandHandler"="{AFA470FE-371D-4F98-9592-39E3C7227E5C}" "Icon"="imageres.dll,-5379" "MUIVerb"="@shell32.dll,-31304" "VerbHandler"="{20D04FE0-3AEA-1069-A2D8-08002B30309D}" "VerbList"=hex(7):57,00,69,00,6e,00,64,00,6f,00,77,00,73,00,2e,00,44,00,72,00,\ 69,00,76,00,65,00,46,00,6f,00,6c,00,64,00,65,00,72,00,2e,00,44,00,69,00,73,\ 00,63,00,6f,00,6e,00,6e,00,65,00,63,00,74,00,4e,00,65,00,74,00,77,00,6f,00,\ 72,00,6b,00,44,00,72,00,69,00,76,00,65,00,00,00,57,00,69,00,6e,00,64,00,6f,\ 00,77,00,73,00,2e,00,44,00,69,00,61,00,6c,00,6f,00,67,00,2e,00,44,00,69,00,\ 73,00,63,00,6f,00,6e,00,6e,00,65,00,63,00,74,00,4e,00,65,00,74,00,77,00,6f,\ 00,72,00,6b,00,44,00,72,00,69,00,76,00,65,00,00,00,00,00 "VerbName"="disconnectNetworkDrive" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.DisconnectNetworkDrive\command] "DelegateExecute"="{EDEA4743-46D4-4C14-B358-64FD126052EC}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.DiskFormat] "CanonicalName"="{7FC37423-685D-4719-813A-96F4F22E3FBD}" "CommandStateHandler"="{EDEA4743-46D4-4C14-B358-64FD126052EC}" "CommandStateSync"="" "Description"="@shell32.dll,-37489" "Icon"="imageres.dll,-5330" "ImpliedSelectionModel"=dword:00000001 "MUIVerb"="@shell32.dll,-37488" "VerbHandler"="{20D04FE0-3AEA-1069-A2D8-08002B30309D}" "VerbName"="format" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.DiskFormat\command] "DelegateExecute"="{EDEA4743-46D4-4C14-B358-64FD126052EC}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.DriveFolder.DisconnectNetworkDrive] "CanonicalName"="{7900773F-4D29-453E-AAD0-BB20C5812C34}" "CommandStateHandler"="{EDEA4743-46D4-4C14-B358-64FD126052EC}" "CommandStateSync"="" "VerbHandler"="{20D04FE0-3AEA-1069-A2D8-08002B30309D}" "VerbName"="disconnectNetworkDrive" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.DriveFolder.DisconnectNetworkDrive\command] "DelegateExecute"="{EDEA4743-46D4-4C14-B358-64FD126052EC}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.edit] "CanonicalName"="{CBF5DF40-0DF5-4e8b-B35B-D008E96E468C}" "Description"="@shell32.dll,-37399" "Icon"="imageres.dll,-5306" "InvokeCommandOnSelection"=dword:00000001 "MUIVerb"=hex(2):40,00,73,00,68,00,65,00,6c,00,6c,00,33,00,32,00,2e,00,64,00,\ 6c,00,6c,00,2c,00,2d,00,33,00,37,00,33,00,39,00,38,00,00,00 "ResolveLinksQueryBehavior"=dword:00000000 "ShowAsDisabledIfHidden"="" "StaticVerbOnly"="" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.Eject] "CanonicalName"="{F3B3A150-632D-4529-999F-F8A6575966D7}" "CommandStateHandler"="{EDEA4743-46D4-4C14-B358-64FD126052EC}" "Description"="@shell32.dll,-31376" "Icon"="imageres.dll,-5328" "ImpliedSelectionModel"=dword:00000001 "MUIVerb"="@shell32.dll,-31382" "ResolveLinksQueryBehavior"=dword:00000000 "VerbHandler"="{20D04FE0-3AEA-1069-A2D8-08002B30309D}" "VerbName"="eject" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.Eject\command] "DelegateExecute"="{EDEA4743-46D4-4C14-B358-64FD126052EC}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.email] "CanonicalName"="{6D3EBC98-4515-4E78-B947-EE713A788CF2}" "CommandStateHandler"="{3756e7f5-e514-4776-a32b-eb24bc1efe7a}" "CommandStateSync"="" "Description"="@shell32.dll,-31371" "Icon"="shell32.dll,-265" "MUIVerb"="@shell32.dll,-31370" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.email\DropTarget] "CLSID"="{9E56BE60-C50F-11CF-9A2C-00A0C90A90CE}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.encrypt-bde] "CanonicalName"="{b2b2f1fc-fc61-4e11-823a-e97c7f66e041}" "InvokeCommandOnSelection"=dword:00000001 "MUIVerb"=hex(2):40,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,\ 6f,00,74,00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,\ 00,66,00,76,00,65,00,77,00,69,00,7a,00,2e,00,64,00,6c,00,6c,00,2c,00,2d,00,\ 39,00,32,00,30,00,00,00 "StaticVerbOnly"="" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.encrypt-bde-elev] "CanonicalName"="{df53b819-1c0f-4ff6-b5ba-7473f3c1d2aa}" "InvokeCommandOnSelection"=dword:00000001 "MUIVerb"=hex(2):40,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,\ 6f,00,74,00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,\ 00,66,00,76,00,65,00,77,00,69,00,7a,00,2e,00,64,00,6c,00,6c,00,2c,00,2d,00,\ 39,00,32,00,30,00,00,00 "StaticVerbOnly"="" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.Enqueue] "CanonicalName"="{50F40BC9-CF0A-4AD9-9759-4A4112817186}" "Description"="@shell32.dll,-37428" "Icon"="imageres.dll,-5343" "InvokeCommandOnSelection"=dword:00000001 "MUIVerb"="@shell32.dll,-37427" "ResolveLinksQueryBehavior"=dword:00000000 "StaticVerbOnly"="" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.EraseDisc] "CanonicalName"="{085A29DF-2718-49B9-9108-A3AF2929DFBA}" "CommandStateHandler"="{EDEA4743-46D4-4C14-B358-64FD126052EC}" "CommandStateSync"="" "Description"="@shell32.dll,-31360" "Icon"="shell32.dll,-262" "ImpliedSelectionModel"=dword:00000001 "MUIVerb"="@shell32.dll,-31359" "ResolveLinksQueryBehavior"=dword:00000000 "VerbHandler"="{20D04FE0-3AEA-1069-A2D8-08002B30309D}" "VerbName"="erase" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.EraseDisc\command] "DelegateExecute"="{EDEA4743-46D4-4C14-B358-64FD126052EC}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.EraseDisc.Action] "ActionId"="Explorer.EraseDisc" "CanonicalName"="{03D6AE19-AEA3-4F04-B2A6-A0D1A01B8DA1}" "CommandStateSync"="" "CommandStore"="Windows.EraseDisc" "ExplorerCommandHandler"="{9C07355E-C50A-45D2-B4A3-0A8235F8047F}" "ImpliedSelectionModel"=dword:00000001 [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.fax] "AttributeMask"=dword:40000000 "AttributeValue"=dword:40000000 "CanonicalName"="{82180763-66b9-4261-bfd4-43059e1b5cc1}" "Description"="@explorerframe.dll,-14419" "DescriptionTitle"="@explorerframe.dll,-14420" "Icon"="shell32.dll,-1005" "ImpliedSelectionModel"=dword:00000000 "MUIVerb"="@explorerframe.dll,-14418" "SendToVerb"="Fax Recipient.lnk" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.FinishBurn] "CanonicalName"="{e6562de7-3c79-4d4d-aab6-3e3d10ff9818}" "CommandStateHandler"="{E410F8AE-00A1-4A1B-8247-924705718354}" "CommandStateSync"="" "Description"="@shell32.dll,-31392" "Icon"="imageres.dll,-5329" "MUIVerb"="@shell32.dll,-31391" "VerbHandler"="{6ea07e8a-40be-4d20-b699-f0806b4bea83}" "VerbName"="burn" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.FinishBurn\command] "DelegateExecute"="{E410F8AE-00A1-4A1B-8247-924705718354}" [HKEY_LOCAL_MACHINE\pe-SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.folderoptions] "CommandStateSync"="" "Description"="@shell32.dll,-31449" "ExplorerCommandHandler"="{83bb272f-7d5e-4b6e-9250-889893f0dac7}" "Icon"="shell32.dll,-274" |

离线修复winxshell自带类资源管理器不能打开and离线补回winxshell自带类资源管理器里.zip
20.17 KB, 下载次数: 3, 下载积分: 无忧币 -2
离线修复winxshell自带类资源管理器不能打开and离线补回winxshell自带类资源管理器里的组织按钮和功能列表

CrazeNewBin疯牛病注册表专修20221001.7z
667.15 KB, 下载次数: 2, 下载积分: 无忧币 -2
精简software用的疯牛病专修工具可精简不带dwm的software和带dwm的software
本帖最后由 sairen139 于 2022-10-30 18:01 编辑 sairen139 发表于 2022-10-29 09:37 pe里调整界面大小后保存这一项注册表修改后离线导入df注册表配置文件即可(MRUListEx的值是必须的辅助值不能少这个但值可固定) Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\df\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU] "0"=hex:57,00,69,00,6e,00,58,00,53,00,68,00,65,00,6c,00,6c,00,2e,00,65,00,78,\ 00,65,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\ 00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\ 00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\ 00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\ 00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\ 00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\ 00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\ 00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\ 00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\ 00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\ 00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\ 00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\ 00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\ 00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\ 00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\ 00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\ 00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\ 00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\ 00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\ 00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,18,00,00,\ 00,18,00,00,00,9c,00,00,00,40,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\ 00,00,00,00,52,00,00,00,11,00,00,00,d1,04,00,00,a1,02,00,00,00,00,00,00,00,\ 00,00,00,00,00,00,00,00,00,00,00,01,00,00,00,00,00,00,00 "MRUListEx"=hex:00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,ff,\ ff,ff,ff |
| 感谢分享 |
|
本帖最后由 sairen139 于 2022-10-29 06:53 编辑 关于预览窗格功能问题需要进一步研究的帖子:https://www.anquanke.com/post/id/255690 如何利用Windows预览机制实现持久化 本文是翻译文章,文章原作者 specterops,文章来源:posts.specterops.io,原文地址:https://posts.specterops.io/life-is-pane-persistence-via-preview-handlers-3c0216c5ef9e  用户对文件在Explorer中的布局有各自独特的偏好。有些人喜欢紧凑的详细信息视图,有些人喜欢带有详细信息窗格的内容视图,还有些人甚至会喜欢使用小图标。Explorer提供了各种自定义选项,允许Windows用户以各种方式查看文件系统的内容,然而我们特别感兴趣其中的一个功能:预览窗格(Preview Pane)。 预览窗格允许用户快速浏览所选文件的内容,不需要实际打开该文件。该功能在Windows 10中默认禁用,但可以通过Explorer的查看->预览窗格菜单中启用。 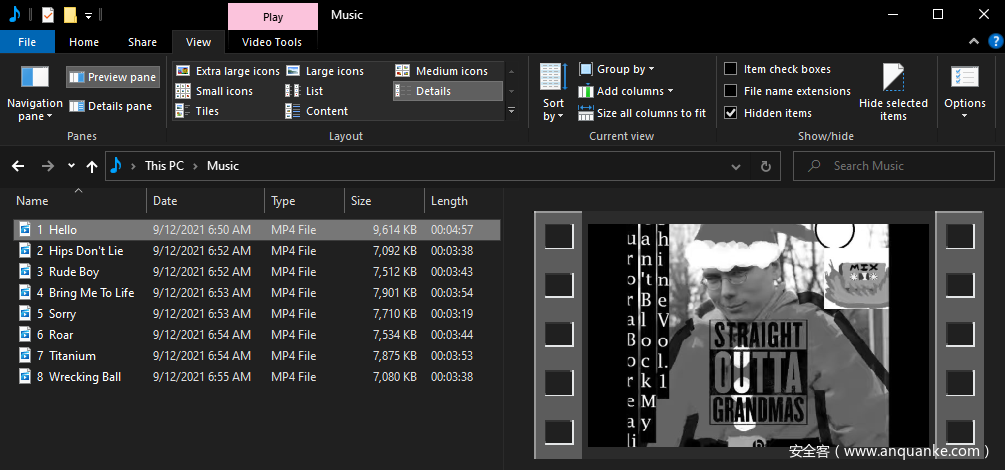 这个功能表面上看起来比较简单,但事实并非如此。比如,Windows如何知道怎么显示某些文件类型的内容,不显示其他文件类型呢?预览视图是由Explorer来控制,还是在另一个进程中完成呢?这些处理器(handler)是否可以被滥用呢?我们花了几天事件来探索资源管理器预览处理器,想深入了解这些处理器的工作原理,回答上述问题。 0x01 工作原理我们研究的第一步,是想澄清Explorer在将文件的预览信息呈现给用户时到底执行了哪些操作。首先我们启用预览窗格,导航到某个文件夹,该文件夹包含能够展示预览视图的一些文件类型(我们使用的是.CONTACT文件类型,该类型默认已安装在Windows上,大家还可以使用其他类型),然后运行Procmon以及Process Hacker,观察系统的行为。虽然我们并没有得到完整的信息,但总结出了以下几点: 1、Explorer首先会在HKCU中查找{8895b1c6-b41f-4c1c-a562–0d564250836f}子键,获取默认值,以便查询关联文件类型的预览处理器(如果未找到则继续寻找HKCR)。 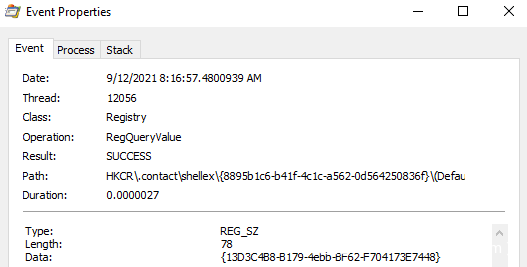 2、Explorer查询在已注册的预览处理器列表中与该扩展(.CONTACT文件对应的是{13D3C4B8-B179–4ebb-BF62-F704173E7448})关联的CLSID值。预览处理器列表位于HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\PreviewHandlers\中,根据微软官方说明,该列表主要用于系统优化。 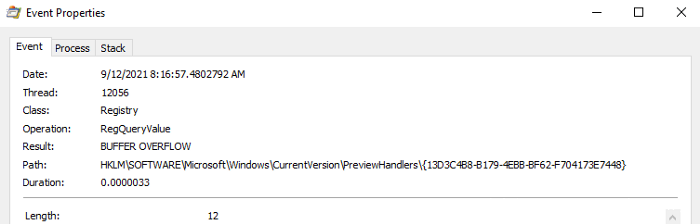 3、随后Explorer会查询CLSID的InProcServer32值。 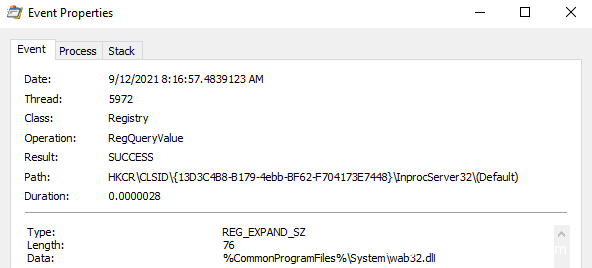 4、Explorer会将后续事务交给DCOM Server Process Launcher服务(DcomLaunch)来处理,该服务会收集与CLSID关联的AppID。 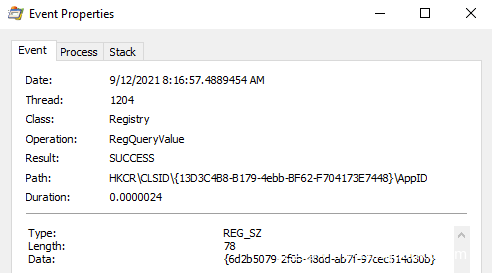 5、DcomLaunch会引用与AppID(位于HKCR\AppID\)对应的DllSurrogate值。需要注意的是,{6d2b5079–2f0b-48dd-ab7f-97cec514d30b}是系统原生x64预览处理器的默认值。WOW64处理器使用的是{534A1E02-D58F-44f0-B58B-36CBED287C7C}。 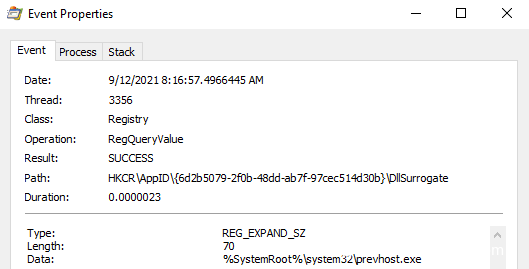 6、随后DcomLaunch会启动代理进程PREVHOST.EXE,传入命令行参数:{HANDLER-INPROCSERVER32-CLSID} -Embedding。 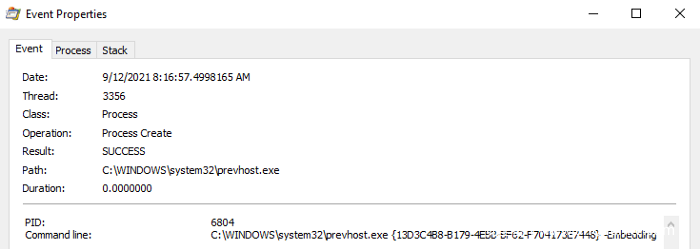 7、PREVHOST.EXE加载CLSID引用的进程内COM服务器。  8、PREVHOST.EXE打开待预览的文件。 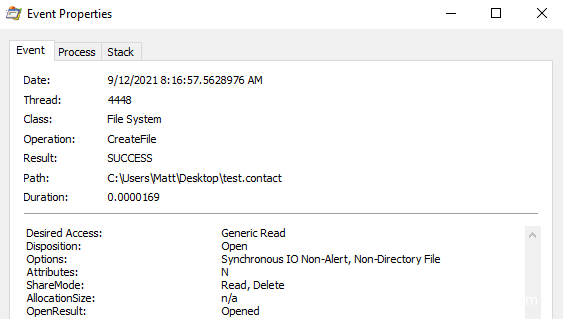 此时,预览处理器DLL会被映射到代理进程PREVHOST.EXE中,文件会被处理,传回Explorer的预览窗格。如前文所述,在句柄加载期间以及加载之后,我们有很多小细节没有覆盖到,但此时我们已经知道如何滥用这个过程了。 0x02 构造处理器现在我们已经了解了大致的处理流程,我们可以着手构造自己的预览处理器。值得庆幸的是,微软发布了一些非常有用的文档和示例代码,可以作为参考。虽然官方提供的资源非常有用,但主要是面向开发者在生产环境中的指南,包含大量冗余代码(比如根据预览窗格大小自适应地调整预览大小)。 我们只需要最小的一个示例来测试我们的理论,因此我们写了一个基本的进程内COM服务端,根据微软文档,实现了IPreviewHandler以及IInitializeWithStream接口。虽然微软表示还需要实现IObjectWithSite、IOleWindow以及IPreviewHandlerVisuals接口,我们发现如果只关心处理器内代码执行逻辑的实现,不关心在面板中渲染完整预览视图时,那么就不需要实现这些接口。为了测试构造的处理器,当IPreviewHandler::DoPreview()调用我们的渲染函数时,我们只是简单地弹出一个消息框。 由于这些逻辑都与COM有关,我们修改了注册表,构造所需的所有键值,以便处理器能在主机上正常运行。这里微软的文档也提供了很多帮助,但我们并不确定实际需求与最佳实践之间的区别。我们发现需要如下注册表键值,才能弹出我们的测试消息框:  此时,我们已经创造了能工作的一个最简单POC,这个预览处理器关联的是.SPECTEROPS文件。  这种技术最大的障碍在于,默认情况下,预览处理器会在PREVHOST.EXE低完整性级别的实例中运行。这意味着即使我们可以执行代码,我们的令牌完整性级别(IL)也会限制我们访问在后续活动中访问操作系统的重要信息。 值得庆幸的是,微软自己也意识到在很多情况下,在低IL下运行对某些开发者来说是不可行的(比如需要将文件保存到带有中等完整性标签的目录中)。为了支持这些用例,开发者允许选择性退出低IL的隔离域,托管在PREVHOST.EXE代理进程的中等IL实例中。要实现这一点,微软指示开发者要在HKCR\CLSID\{PREVIEW-HANDLER-CLSID}中创建一个新的值DisableLowILProcessIsolation,并将值设置为1。 由于HKCR实际上只是HKCU\Software\Classes以及HKLM\Software\Classes的组合,因此理论上开发者应该能够在当前用户上下文中,在HKCU创建所需的注册表键值、注册预览处理器。当用户预览所选择的文件类型时,对应的处理器就可以在中等IL级别中运行。为了测试这个理论,我们在先前注册的预览处理器中添加了DisableLowILProcessIsolation值,设置对应的值并刷新预览窗格后,我们发现自己仍运行在低IL中。 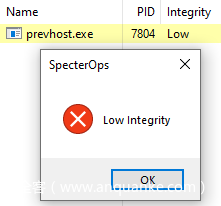
为了澄清这个问题,我们运行Procmon,设置注册表操作过滤器,过滤以DisableLowILProcessIsolation结尾的路径。我们再次刷新预览窗格,但没有看到任何信息。在尝试其他几种文件类型后,Procmon终于捕捉到EXPLORER.EXE查询该键值的行为。这个事件对应的调用栈如下所示: 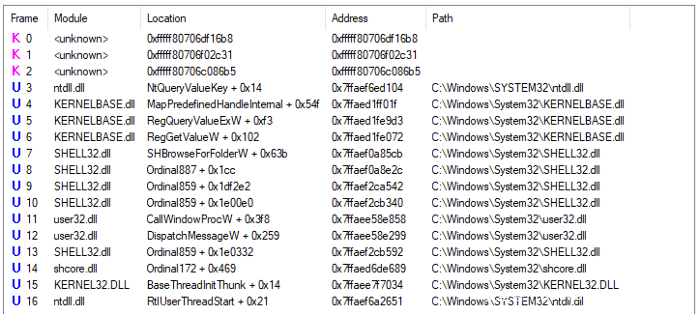 Procmon的符号解析在这里有点问题。对我们来说,第7帧(SHELL32!SHBrowseForFolder+0x63b)最为有趣,因为该条目对应的是函数SHELL32!DoesExtensionOptOutOfLowIL内的一个地址。该函数的反汇编代码如下所示: 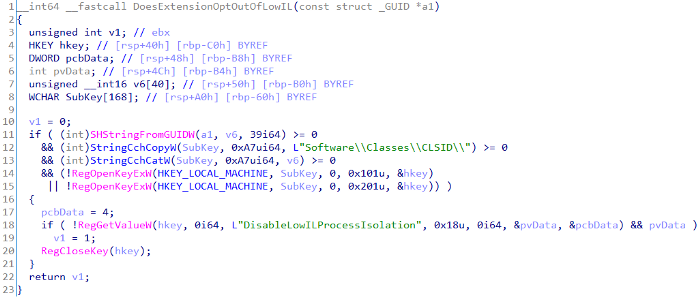 观察这段代码,我们马上就知道哪里出了问题:系统只检查了HKLM下的注册表键值。这不但宣告了我们先前针对每个用户的持久性策略的失败,同时因为只有管理员能够写入HKLM,我们也无法以普通用户身份绕过低IL隔离机制。我们探索了微软提供的一个独立代理进程来托管我们的处理器,但由于这些进程也是以低IL来运行,因此这条路也行不通。 尽管这并不理想的结果,我们仍然得到了一种持久化机制,可以将自己的代码托管在微软签名的可执行文件中。由于需要一定权限,这种方式很少在初始化攻击中使用,而是会在获取更多权限后才涉及。此外,由于我们针对的是HKLM,系统中的所有用户都会受到影响,不单单是当前的用户。 0x04 具体操作为了充分利用这种技术,我们的工具会分解成3个不同的组件:载荷、目标文件以及释放器。 1、载荷:处理器DLL,在代理进程中加载,开始执行我们的恶意代码。载荷会被释放到磁盘中用户定义的位置。 2、目标文件:扩展名与我们设置的处理器相匹配的文件。该文件同样会被释放到磁盘的任意位置,但最好释放到用户很有可能通过Explorer浏览到的位置。 3、释放器:负责释放载荷和目标文件(可选),设置所需的注册表键值,强制EXPLORER.EXE预览目标文件,运行我们的代码。释放器通过C2运行在内存中。 处理器内运行的函数不再使用测试消息框,而是换成shellcode运行程序。这部分内容留给大家完成,但还是需要考虑到一些问题: 1、通过程序操作的方式启用预览窗格后,Explorer必须重启,不然处理器不会被运行。 2、由于可能会运行多个处理器实例,因此需要某种类型的互斥锁,避免出现非预期行为。 3、可以无缝劫持现有的处理器,但由实现上的差异(比如Word会根据文件扩展名来使用不同的ProgID,而不是CLSID),撤销劫持并不是想象中的那么简单。 0x05 PoC整个攻击的PoC可参考此处视频。 0x06 检测方式这种技术的检测方式很大程度上需要依赖对注册表改动操作。在开发这项技术的过程中,我们澄清了实现这种持久化技术的基本条件。虽然我们可以监控大量的特征常量,但攻击者有各种方式可以破坏检测逻辑(比如使用ProgID,而不是CLSID)。这里我们首先介绍一下最基本的检测条件,然后再讨论能让检测更加稳健的一些限定条件。 这里很重要的一点是:攻击者不需要为新文件类型实现一个预览处理器,可以按照大致相同的路线,简单地劫持已有的处理器即可。 基本条件为了让这种技术能够发挥作用,又具备足够权限(即不在低IL下执行),我们在构造基本检测能力时,可以将关注点集中在几个特定的注册表项上。 需要监控的第一个也是最重要的一个事件:在HKLM\Software\Classes\CLSID\*的任意注册表项中将DisableLowILProcessIsolation值设置为1。攻击者必须在HKLM中设置这个值,以便在中等IL中启动代理进程,以便作为普通用户与主机进行交互。虽然这个事件覆盖的范围比较大,但经过测试,我们发现对这个值的操作实际上相当罕见。 第二个注册表键值为HKCR\Software\Classes\*\ShellEx\{8895b1c6-b41f-4c1c-a562–0d564250836f},创建这个键值是在系统上安装预览处理器的基本条件。这个键值可以用于任何文件类型,包括现有的或者新的扩展名,但必须被设置。要注意的是,我们必须使用通配符过滤器,而不是将范围限定为.*,避免将检测限制在文件扩展名上。这是因为注册表中的文件类型(比如.foo)可以与ProgID关联(比如foo),这些ProgID仍然可以发挥相同的作用。 最后一个基本条件是将预览处理器的CLSID作为值,添加到HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\PreviewHandlers键(用于特定用户)或者HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\PreviewHandlers(用于所有用户)。这个值用来指定预览处理器的友好名称,但不一定需要设置。 分类条件虽然基本条件提供了少量的事件,可以识别预览处理器的安装操作,但还有其他一些条件,可以提供关联的上下文信息。 第一个条件是必须启用Explorer的预览窗格,这是这种攻击技术的必备条件。我们需要将这个条件当成一个可选事件,因为用户可能已经启用了该功能,这样就不会出现注册表操作事件。预览窗格默认处于禁用状态,对窗格的启用操作可以协同判断攻击者的行为。我们可以监控HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Modules\GlobalSettings\DetailsContainer,判断DetailsContainer的值是否被设置为02 00 00 00 01 00 00 00,同时监控HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Modules\GlobalSettings\Sizer,判断DetailsContainerSizer是否被设置为15 01 00 00 01 00 00 00 00 00 00 00 6d 02 00 00。正常情况下,只有EXPLORER.EXE才会设置这些键值。 我们还可以监控正在设置的代理进程。代理进程正常情况下是PREVHOST.EXE,但攻击者可能会在系统中注册自己的进程,以便自定义应用能处理预览,(比如某个托管处理程序需要加载特定版本的公共语言运行时(CLR))。代理进程能够帮助攻击者规避基于进程或者文件的检测机制。AppID应该在HKLM\Software\Classes\CLSID\*中设置,如果使用的是默认的PREVHOST.EXE,那么x64处理器对应的应该为{6d2b5079–2f0b-48dd-ab7f-97cec514d30b},在x64主机上运行的x86处理器应该为{534a1e02-d58f-44f0-b58b-36cbed287c7c}。如果攻击者选择使用自己的代理进程,那么必须创建HKLM\Software\Classes\AppId\*,并且DllSurrogate的值应该设置为自定义应用的路径。无论使用哪个代理进程,该进程始终会使用命令行参数{MALICOUS-HANDLER-CLSID} -Embedded来启动,其中CLSID为已注册的处理器DLL对应的值。 最后一点,要关注预览处理器DLL本身的注册行为。攻击者需要设置HKLM\Software\Classes\CLSID\*\InProcServer32的默认值,只想磁盘上的路径。需要注意的是,这个事件可能相对而言会比较多一些。此外,DLL文件在安装时不一定需要存在,可以在攻击者准备好后随时释放。 SQL查询示例index=azure_mdatp sourcetype="mdatp:DeviceRegistry" AND registry_path="HKLM\Software\Classes\CLSID\*"[search index=azure_mdatp sourcetype="mdatp:DeviceRegistry" registry_path="HKLM\Software\Classes\CLSID\*" AND registry_value_name="DisableLowILProcessIsolation" action_type=RegistryValueSet]AND [search index=azure_mdatp sourcetype="mdatp:DeviceRegistry" registry_path="HKLM\Software\Classes\CLSID\*" AND action_type=RegistryKeyCreated registry_key_name="HKCR\Software\Classes\*\ShellEx\{8895b1c6-b41f-4c1c-a562–0d564250836f}"]AND [search index=azure_mdatp sourcetype="mdatp:DeviceRegistry" registry_path="HKLM\Software\Classes\CLSID\*" AND action_type=RegistryKeyCreated registry_key_name="HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\PreviewHandlers"]| stats count values(host) as host dc(host) as host_count by registry_key_name | sort - count | where host_count < 5| fillnull value=0| `HumanTime(_time)`| table HumanTime, _time, host, device_id, ContainerName, registry_key_name, process_exec, clean_path, registry_value_data, account_domain |
| 那个PE有大大分享的这个资源管理器啊 求成品 我想试试! |
| 留个记号,回头试试 |
sairen139 发表于 2022-10-27 22:05 离线挂载DEFAULT注册表配置文件为df导入片段开机直接展开导航栏此电脑下面的分区最方便 Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\df\Software\Microsoft\Windows\CurrentVersion\Explorer\Modules\NavPane] "ExpandedState"=hex:04,00,00,00,16,00,14,00,1f,80,cb,85,9f,67,20,02,80,40,b2,\ 9b,55,40,cc,05,aa,b6,00,00,01,00,00,00,4d,00,00,00,1c,00,00,00,31,53,50,53,\ a6,6a,63,28,3d,95,d2,11,b5,d6,00,c0,4f,d9,18,d0,00,00,00,00,2d,00,00,00,31,\ 53,50,53,35,7e,c7,77,e3,1b,50,43,a4,8c,75,63,d7,27,77,6d,11,00,00,00,02,00,\ 00,00,00,0b,00,00,00,ff,ff,00,00,00,00,00,00,00,00,00,00,16,00,14,00,1f,60,\ 98,3f,fb,b4,ea,c1,8d,42,a7,8a,d1,f5,65,9c,ba,93,00,00,01,00,00,00,4d,00,00,\ 00,1c,00,00,00,31,53,50,53,a6,6a,63,28,3d,95,d2,11,b5,d6,00,c0,4f,d9,18,d0,\ 00,00,00,00,2d,00,00,00,31,53,50,53,35,7e,c7,77,e3,1b,50,43,a4,8c,75,63,d7,\ 27,77,6d,11,00,00,00,02,00,00,00,00,0b,00,00,00,ff,ff,00,00,00,00,00,00,00,\ 00,00,00,16,00,14,00,1f,50,e0,4f,d0,20,ea,3a,69,10,a2,d8,08,00,2b,30,30,9d,\ 00,00,01,00,00,00,4d,00,00,00,1c,00,00,00,31,53,50,53,a6,6a,63,28,3d,95,d2,\ 11,b5,d6,00,c0,4f,d9,18,d0,00,00,00,00,2d,00,00,00,31,53,50,53,35,7e,c7,77,\ e3,1b,50,43,a4,8c,75,63,d7,27,77,6d,11,00,00,00,02,00,00,00,00,0b,00,00,00,\ ff,ff,00,00,00,00,00,00,00,00,00,00,16,00,14,00,1f,54,25,48,1e,03,94,7b,c3,\ 4d,b1,31,e9,46,b4,4c,8d,d5,00,00,01,00,00,00,4d,00,00,00,1c,00,00,00,31,53,\ 50,53,a6,6a,63,28,3d,95,d2,11,b5,d6,00,c0,4f,d9,18,d0,00,00,00,00,2d,00,00,\ 00,31,53,50,53,35,7e,c7,77,e3,1b,50,43,a4,8c,75,63,d7,27,77,6d,11,00,00,00,\ 02,00,00,00,00,0b,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00 |
| 建议88mb的骨头网络版pe把控制面板界面恢复出来,用习惯了 |
| 一般来说pe还是选择第三方文件管理器为好,第三方文件管理器选择的余地更大功能也更多更强大! |
Powered by Discuz! X3.3
© 2001-2017 Comsenz Inc.